How to Ensure Cybersecurity in the Age of IoT
Without adequate security, all connected devices provide a direct gateway into our personal & professional networks. Is it possible to avoid theft of data?
Considering the pace we are all moving at, companies are continually striving to make everything connected virtually. Devices connected to IoT can ‘communicate’ with each other be it tech gadgets, smart phones, smart home equipment and machines, etc. But, without adequate security, these connected devices provide a direct gateway into our personal, corporate, and governmental networks where confidential data can be either stolen or destroyed.
Now that IoT has become a complete game-changer, cybersecurity is more relevant than ever and challenging at the same time. The question still remains, are we ready for such an increased level of connectivity? What are the IoT security risks?
Before we dive into the glaring security issues, let’s look at some IoT market statistics, shall we?
Essential Internet Of Things Statistics To Keep You Up to Speed
Overview of the IoT market
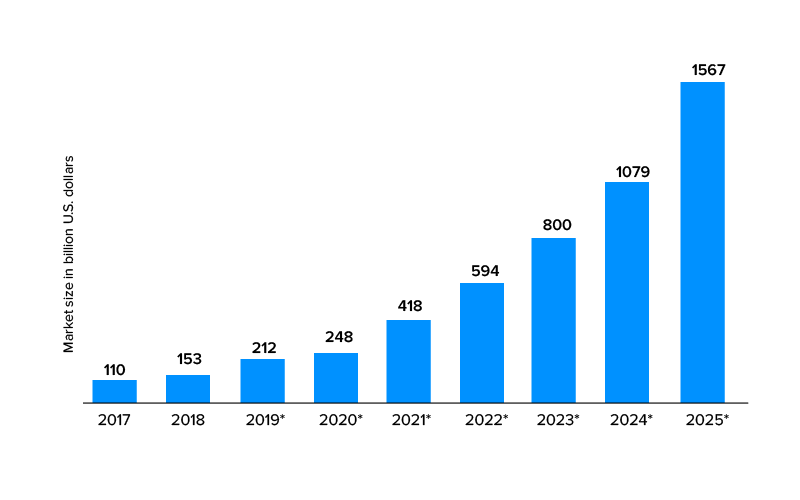
1. The global market for the Internet of things (IoT) reached $100 billion in revenue for the first time in 2017, and forecasts suggest that this figure will grow to around $1.6 trillion by 2025.
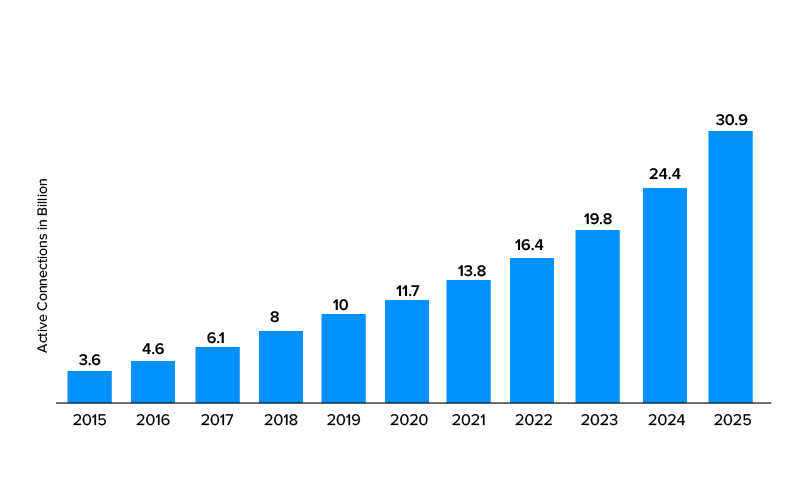
2. The total number of connected devices to IoT is projected to reach to 30.9 billion worldwide by 2025. Do note that this number includes active nodes/devices or gateways that concentrate the end-sensors, rather than consumer devices such as computers and cell phones.
3. Due to the Covid-19 pandemic, the IoT adoption rate has increased, especially in the IoT in healthcare setup.
According to Microsoft’s 2020 IoT signals report, one-in-three decision-makers plan to up their IoT investments while 41% say their existing investments will remain the same.
Statistics about IoT security threats
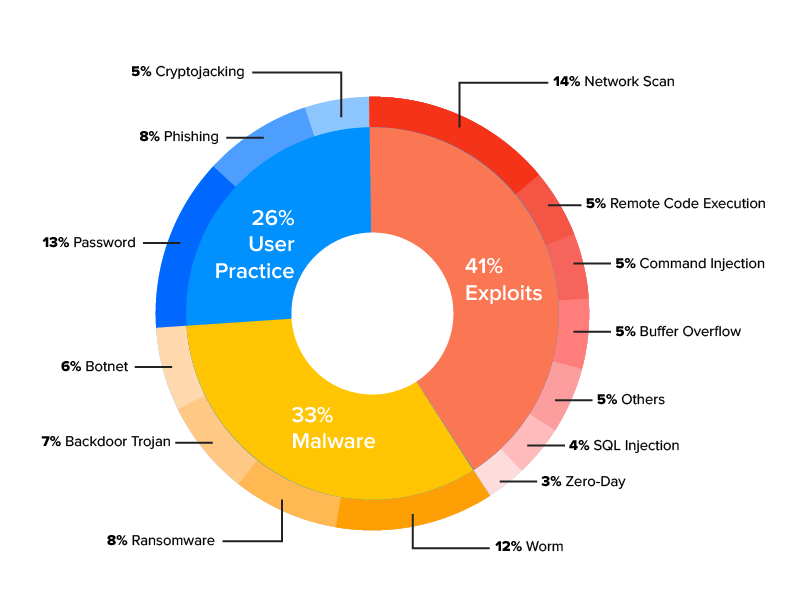
1. SonicWall, which blocks an average of 26 million malware attacks globally each day, recorded 40% rise in malware attacks during the third quarter of 2020 as compared to 151.9 million ransomware attacks globally through the first three quarters of 2019, marking 15% and 5% year-over-year declines, respectively. The report clearly indicates how IoT cyber security is compromised.
2. According to the 2020 Unit 42 IoT threat report, 98% of all IoT device traffic is unencrypted, exposing personal and confidential data on the network. This is one huge example of IoT cyber risk.
3. The same report also points out that 57% of IoT devices are vulnerable to medium- or high-severity attacks. Also, 41% of attacks exploit device vulnerabilities that again shows IoT security challenges.
Now that you are up to date with all the data that revolves around security aspects in IoT, let’s discuss the challenges of securing IoT devices.
Internet Of Things Security Vulnerabilities And Challenges
1. Insufficient testing and updating
The major issue that comes with companies while developing IoT devices is that no one takes care of the security issue unless some major problem hits. Once IoT manufacturers launch a device they ensure that it is secure but over time it becomes prone to hackers and other security issues due to the lack of constant testing and updating. Hence, opening the door to IoT security challenges.
2. Lack of compliance on the part of IoT manufacturers
Let me explain this with examples you see in your day to day life. If you use fitness trackers, you must have noticed that bluetooth remains visible after the first pairing. A smart refrigerator can expose gmail credentials and a smart fingerprint padlock can be accessed with a Bluetooth key that has the same MAC address as the padlock device.
This can be labeled as one of the biggest IoT cyber security threats! Below are some security issues in IoT devices from manufacturers:
- Weak and easily guessable passwords
- Usage of old operating systems and software
- Insecure and unprotected data storage and transfer
- Technical issues in the hardware
3. Botnet attacks
Cyber security for IoT devices is very crucial since they are highly vulnerable to Malware attacks. They do not have the regular software security updates that a computer does. To perform a botnet attack, a hacker first creates an army of bots by infecting them with malware. Further, directs them to send thousands of requests per second to bring down the target.
Cyber security and IoT should go hand in hand in order to avoid a situation of attack. A botnet attack can easily cause a security threat for transportation systems, manufacturing plants, water treatment facilities and electrical grids, which can threaten big groups of people.
For example: A hacker can create spikes on the power grid by triggering a cooling and heating system at the same time. If this attack is planned on a big-scale it can create a nation-wide power outage.
4. Data security and privacy issues
Did you know that hackers did not spare a visionary like Elon Musk and a company like Apple which is known for its proud security claims. ? If such data comes in the wrong hands, it will not only lead to loss of money but also compromise intellectual property.
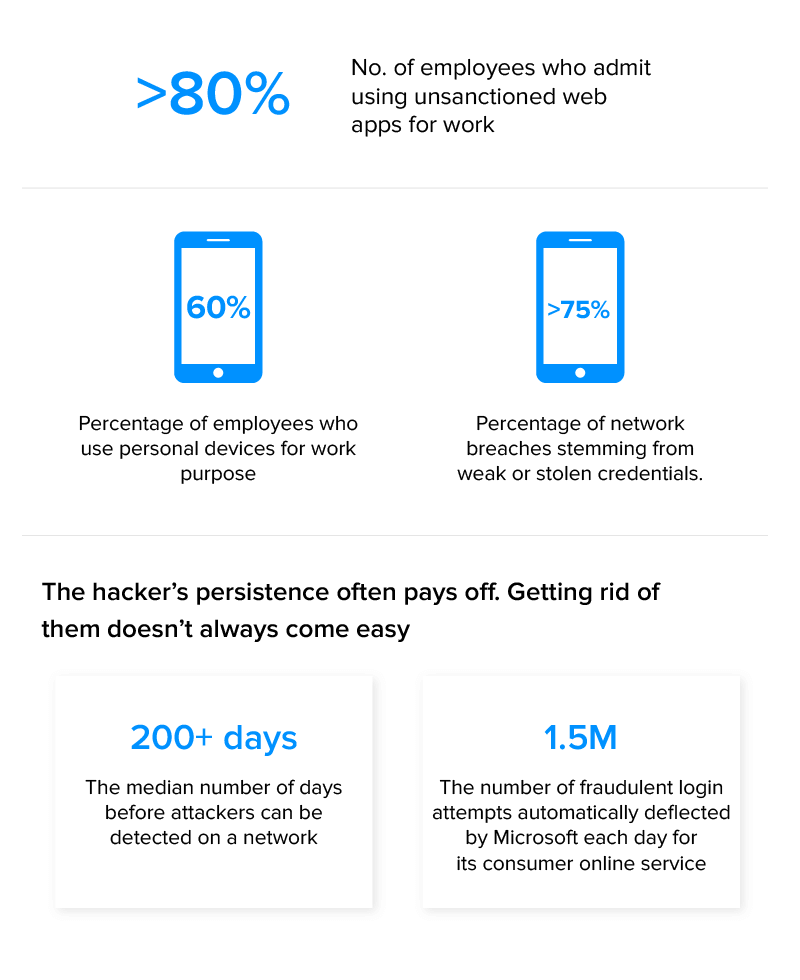
It was predicted that the Internet of Things will become a target-rich environment for hackers by 2020, attracting more than 25% of all cyberattacks. According to Microsoft, security aspects in IoT are lagging because 60% of employees use their personal devices for work purposes, and more than 80% admit to using unsanctioned web apps for work.
5. Financial crimes
Electronic payment companies that deploy Internet of Things may experience a wave of financial crimes. It will be a challenge to ensure the timely detection of fraud.
Also, due to compliance and operational issues, it will be difficult for all financial companies to launch new models of workflow. That is, unless they improve their project lifecycle and risk management strategies that include a rising threat of IoT security breaches.
6. Home invasions
You must be familiar with the concept of ‘smart homes’, which is a by-product of IoT. Cyber security for IoT becomes a huge issue when it comes to home automation. Due to unsafe devices and poor defense mechanisms, your IP addresses are trackable and it makes it easy for hackers to locate the address of the device.
7. Remote smart vehicle access
An IoT security challenge that is close to home invasion is the hijacking of your smart vehicles. This can lead to theft of personal data, vehicle theft, manipulation of safety-critical systems, etc.
Also, remote vehicle access can be a subject to ransomware, as a hacker may demand a hefty fee to unlock the car or to enable the engine. These malicious intrusions are obviously a huge threat to public safety as they can cause accidents.
Now that you have walked through the vulnerabilities and challenges that come with IoT, it’s time to talk about cyber security strategies that can help you overcome them.
How Can You Make IoT Connections Secure?
1. Secure the network
It is extremely important to secure the network that is a connecting bridge between the IoT devices and the back-end systems. This can be achieved by implementing security features like antivirus, anti-malware, firewalls and intrusion detection and prevention systems.
That being said, in order to sustain a smooth operation, there is a need for the IoT network to be protected and secured. You can effectively protect the network and secure it against attacks with the help of the above mentioned systems.
2. Authenticate the IoT devices
One of the cyber security solutions can be device authentication features for the IoT devices. Features like- multi-factor authentication and biometric systems ensure that nobody can access your devices. A potential attacker will need personal information to gain access to information and this is where you have leverage.
It is of great significance to secure your devices and reduce the probability of your data getting into the wrong hands. When you implement the suggested security options, your IoT devices become well secured against external breach of security. Thus, you will be able to enjoy the numerous benefits of having IoT devices at home, in the office, in your automobile, and anywhere you want.
3. Public key infrastructure strategy
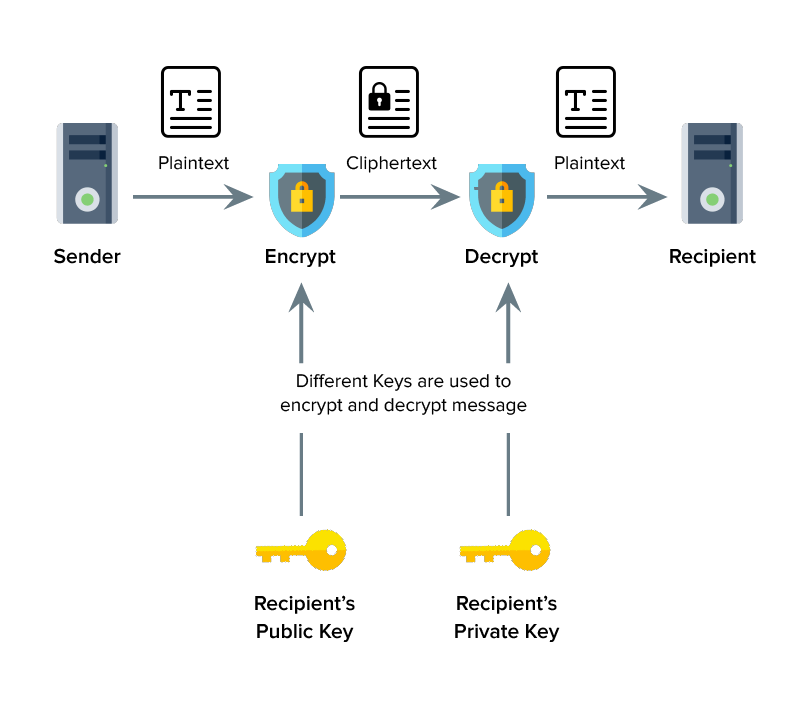
A public key infrastructure (PKI) allows the users to engage in secure forms of communication, data exchange, and money exchange. This type of engagement is carried out using public and private cryptographic key pairs.
PKI ensures the encryption of data through two — asymmetric and symmetric encryption — processes. In asymmetric, we need two keys, one key is the public key and the other key is the private key. If something is encrypted with the public key, then decryption can only be done with the private key and vice-versa.
On the other hand for symmetric both the data encryption and decryption is done with the same key. The data encryption and decryption ensure that data privacy is maintained and the chances of data theft are reduced to the bare minimum.
4. Use IoT security analytics
You can drastically change the number of security issues you face by implementing security analytics. This involves collecting, correlating, and analyzing the data from multiple sources and can help IoT security providers by assisting in identification of potential threats.
Final Say
There is a lot of scope in IoT today and it is safe to say that the market will increase as per the projections, so now is the time to dive deep into the subject and understand it’s what’s and how’s. Also, with the discussion on IoT security challenges and solutions, we can conclude that securing applications is of paramount importance.
The security challenges must be managed, monitored and avoided by taking certain measures. You can go ahead and hire an IoT app development company that can help you overcome all your security risks, you can also choose the company based on the location, for example if you reside in the USA, then finding an iot app development company USA is better choice, as you will be able to know whether the company is genuine and knows its clients and customers choice.

strategies your digital product..