The moment people step out of their homes, they go on a quest for open Wi-Fi networks. Whether they are waiting at the airport or sitting at a cafe, the prime agenda is to find an open Wi-Fi connection.
Scaredly, the hackers are also on the same quest. They too wait for the users to initiate a connection request on the open network before they put their phishing brains into work and deprive them of their sensitive data or worse, money in their bank account.
While HTTPS is effective to some extent, it is an SSL protocol which is known to make users safe by being unbreakable and largely secure. But Man-In-The-Middle (MITM) attacks have found ways to breach this too.
This is where SSL Pinning technique comes into the picture as one of the mobile app security best practices. Talking specifically about platforms, it is the ideal iphone app security solution that does an amazing job solving the issue.
In this article, we are going to look into the types and process of incorporating SSL Pinning in iOS apps for preventing these Man In The Middle attacks. A process that is an active part of the OWASP mobile security testing practice.
Types of SSL Certificates Pinning Method
There are majorly two methods for SSL Pinning test as discussed below:
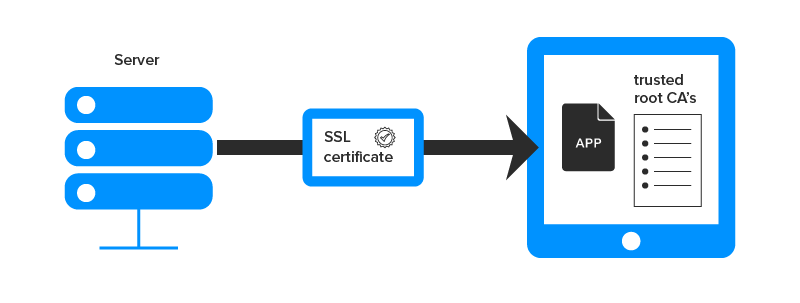
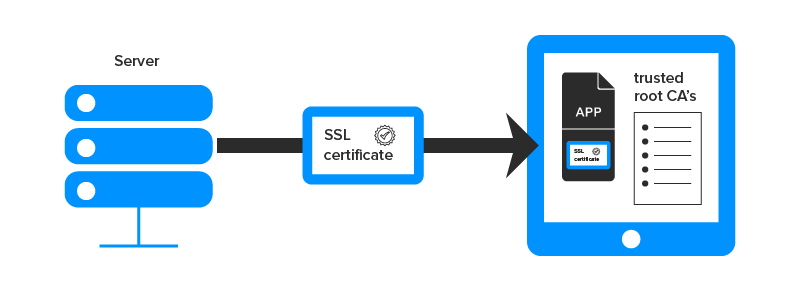
- Pin the certificate – You can download the server’s certificate and bundle them in the app. At the runtime, the app compares the server certificate to ones that you have embedded.
- Pin the public key – You can retrieve the public key of certificate in the code as a string. At the runtime, the application compares the certificate’s public key to one which is hard-coded in the code.
Making a choice from between the two SSL pinning iOS methods is dependent on your server configuration and individual needs. When you choose the first option, you will have to upload the app when the server changes its certificate or it will stop working. When choosing the second option, you might violate the key rotation policy as the public key won’t change.
Let’s now take a look at the steps to implement SSL Pinning in your iOS app.
*Note: The steps mentioned below follow the process of iOS certificate pinning with Swift.
How to Implement SSL Pinning in your iOS App
1. NSURLSession
In the case of NSURLSession, the primary method for handling SSL pinning is URLSession:didReceiveChallenge:completionHandler:delegate. Developers will have to set the class to conform URLSessionDelegate and paste this function to the class:
The function would “request credentials from the delegate in response to an authentication request from the remote server.” The iPhone app developer will then compare certificates from the server with one saved in the app bundle. If the two certificates are found identical, authentication will let it pass and the client will be able to connect to the server.
2. Alamofire Certificate Pinning
Alamofire is one of the most famous libraries for HTTP networking in Swift language. It comes with the built-in functionality for SSL pinning in iOS Swift and is extremely easy to use. Here’s how to make a secure iOS app with Alamofire certificate pinning.
Common Issues Associated With SSL Pinning Implementation & How to Solve Them
The Quality Assurance Experts at reputed app development agencies, regularly test mobile apps for security vulnerabilities, including full network penetration. But there are many app testing agencies that don’t focus on these areas with the same enthusiasm. They seem reluctant when implementing this particular iPhone security solution in their apps.
Here are some of the prevalent reasons behind this –
- One of the biggest disadvantages of SSL pinning in iOS app is its implementation. The process is complex and it can force the developers to write the code again and again and complicate the app building process.
- Pinning iOS SSL certificates which are bound to change regularly can force the developers to update the app binary everytime certificate changes.
- Multiple efforts have to be taken to safeguard the ways to bypass iOS SSL verification.
Noting the repercussions that the stage’s absence can bring, here is how some common pitfalls are avoided by a reliable iPhone app development company.
Testing the pin
Unlike regular app testing where you test whether or not everything works, the method for the SSL pinning test is that you’ll have to check whether something fails. You will have to focus on testing that the app cancels potentially compromised connections. If the app enables communication with a single endpoint, testing will be as simple as making the GET request to an arbitrary state. Ideally, in this case, the app must cancel the connection and the request should fail.
Handling certificate change
Renewing a domain certificate retains the public/private key pair, but this is not always the case. But if you plan the update cycle rightly, you will be able to avoid the downtime for end users.
Before the iOS SSL certificate is made active on the website, you must pin it in the app, in addition to the presently active certificate and then release an update. When we follow this step at Appinventiv to make a secure iOS app, we perform a quick test with the new certificate temporarily and test the app with both the certificates pinned.
FAQs About SSL Pinning in iOS Applications
1. Where to store sensitive data in an iOS app?
The app’s sensitive data should always be stored in iCloud or Keychain in iOS or even in the database after proper encryption.
2. How does SSL work?
SSL Pinning is one of the most common iOS app security tips. But in order to understand what it means, you will first have to know how SSL works.
- A browser attempts to connect with a website which is secured with a SSL. The browser then requests the web server to identify itself.
- Web server then sends the browser its SSL certificate copy.
- The browser checks if the SSL certificate must be trusted. If it can be, a message is sent to the web server.
- Web server then sends back an acknowledgement to begin the SSL encrypted session.
- The encrypted data is then finally shared between the browser and web server.
Ending Thoughts
Although SSL pinning is considered secure and widely used whenever encryption is needed, another layer of protection is always welcomed when building high-risk apps. SSL pinning allows you to verify the server’s identity on top of the SSL chain of trust verification.
With SSL pinning, you can refuse all connections except the ones with the designated server whose SSL certificate we’ve saved into our local bundle. A potential drawback of this is that you need to update the app whenever the server’s SSL key is changed.
In case you are also planning to launch an iOS app with SSL pinning, it can be a good start to consult the best iOS app development company.

strategies your digital product..



