How to Develop a PCI DSS Compliant Fintech Mobile App?
Whether your app is a full-fledged Fintech app like PayPal or whether you are a media streaming app like Netflix which asks users to pay in-app for subscriptions, there is one thing you cannot afford to miss – PCI DSS Compliance.
A failure to look into the PCI security standards which lead to data breach can lead to devastating financial consequences such as fees, fines, and even loss of business. This article encompasses all the basics of PCI compliance for fintech app to help move in the right development direction.
This is what our PCI mobile payment acceptance security guide would entail:
- What is PCI DSS?
- Scope of PCI Compliance Requirements
- Why focus on PCI DSS compliance?
- How to Maintain PCI Compliance?
- Establishing A Plan For Continuous Compliance
- Conclusion
- FAQs About PCI DSS compliant Fintech Mobile App Development
What is PCI DSS?
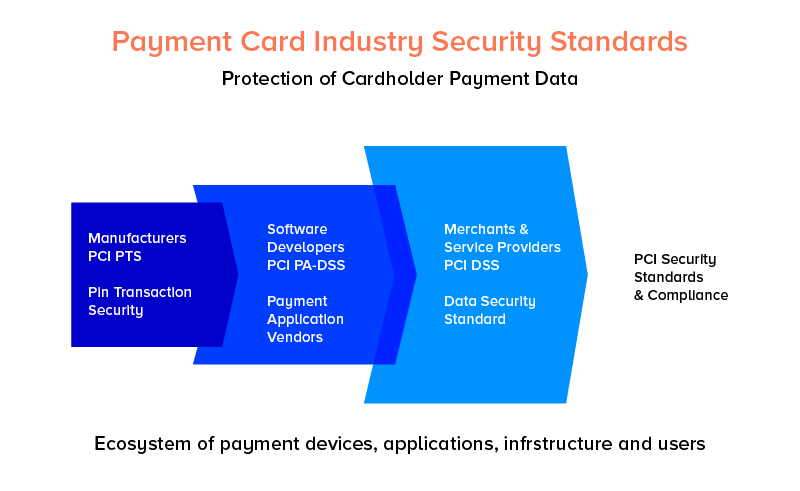
The PCI Payment Card Industry Data Security Standard (PCI DSS) is a heavily prescriptive technical standard that is directed at protecting credit and debit card details, referred to in the industry as ‘cardholder data’. The aim of PCI DSS is to save frauds in terms of payment cards by securing the cardholders’ data inside the organizations that either accept card payments.
PCI compliance centers around Information Technology services. IT-directed compliance managers who are assigned with the purpose of achieving compliance inside the organizations should have required software developer experience and knowledge to assure that PCI compliance mobile app development process meets the PCI DSS requirements checklist.
With the definition of what is PCI DSS now attended, let us look into the fintech app’s specific PCI development requirements.
Scope of PCI Compliance Requirements
Most of the PCI DSS requirements that affect the Fintech app development process fall under Requirements 3, 4, and 6. These requirements cover the storage of cardholder data, encryption practices, access control, and the network security. Let us look into all three of them individually to get a complete understanding of the PCI scope guidance.
PCI Development Requirement 3: Protect Stored Cardholder Data
The cardholder’s data denotes information which is processed, printed, stored, or transmitted on payment card. The apps accepting payment through cards are supposed to protect cardholders’ data and prevent unauthorized usage – irrespective of whether the data is printed on the card or stored locally.
Generally, no cardholders’ data should be stored until it is absolutely necessary for meeting business needs. The sensitive data mentioned on the magnetic stripe should never be stored and in case you will have to store the PAN details, it should be rendered unreadable. Here are some other things that should be accounted for in the PCI compliance checklist looking into requirement 3.
3.1
The data storage and retention time should be limited according to the legal and business purposes, as documents in the data retention policy. All the unnecessary data should be purged at least every quarter.
3.2
Sensitive authentication data should not be stored after authorization, even if its encrypted. Though, issuers can store the authentication data if there is a viable business justification and the data is stored in a secure manner.
3.3
PAN should be masked when displayed. The first six or the last four digits are the only ones which you should display.
3.4
PAN should be rendered unreadable wherever it is stored – this includes digital media, in logs, backup media, and the data received from wireless networks. The technology solutions that we propose for this point at Appinventiv is including a strong one-way hash function of the complete PAN, strong cryptography, index token with highly secured stored pads, etc.
3.5
The keys which are used for the encryption of cardholder data should be protected against misuse and disclosure.
3.6
Companies should completely document and implement the appropriate key management procedure and process for the cryptographic keys which are used for the encryption of the cardholders’ data.
PCI Development Requirement 4: Encrypt the transmission of cardholders’ data across public, open networks
It is not particularly impossible for hackers to intercept the transmission of the cardholders’ data over the open, public networks and it is very important to protect the app’s private data from them. One way to do that is through encryption of the data.
4.1
App development companies should use strong security protocols and cryptography like TLS/SSL Pinning in iOS app and Android solutions safeguarding the cardholders’ sensitive data during its transmission over public network.
4.2
Unprotected PANs should never be sent by the end users’ messaging technologies.
PCI Development Requirement 6: Develop and Maintain Secure Applications
The PCI requirements for fintech app is in terms of the development of external and internal application which is considered to be in scope of the PCI DSS mobile app compliance – this stands for every developed app which processes, stores, and transmit the cardholders’ data.
The PCI payment applications which are created by the Fintech development companies for use by external organizations should comply with the Payment Application Data Security Standard (PA-DSS), and should be assessed by PA-QSA.
6.1
Compliance with the 6.1 requirement calls for a properly documented software asset register of libraries and tools, which are used in software development cycle. Every item inside the software asset register should include:
- A version number
- How and where software is used
- Clear explanation of the function they provide.
Since the software libraries and tools are updated frequently, it is of prime importance that the register is reviewed continuously and is kept up to date.
Once a software asset register is established, a process should be implemented to regularly monitor every item in the register for sending notification of vulnerabilities and the updated releases.
Requirement 6.1 also calls for a risk ranking, which should be assigned for every vulnerability that is identified in the items within the asset register. The vulnerabilities should be risk assessed and must be labeled with risk rating label termed as “Critical,” “High,” “Medium” or “Low.” These risk levels would then help with prioritization of patching.
6.2
This requirement builds upon the vulnerability monitoring and demands the critical level security patches to be addressed and applied within one month of vendor’s release date.
The vulnerabilities patches which are rated at the low levels should be applied in 2 to 3 months of the release.
A log of the patching release monitoring and patching process should be maintained for ensuring that the patches are identified and incorporated within the stipulated time.
6.3
It requires using a software development life cycle that is based on the industry’s best practices. Every part of the software development lifecycle should be documented with details on how mobile app security and PCI requirements are addressed in the conceptualization, design, research, and app testing processes of development.
The PCI payment application development document should be descriptive enough to cover parts of how the app processes, shares, and stores the cardholder data. In order to achieve 6.3 compliance, the aim should be to make documentation descriptive enough for even the third party developers to understand it.
In order to make sure that the developers are adhering to the development lifecycle, completion of every development stage should be documented and audits should be conducted of the development process regularly.
- 6.3.1: The test or custom app accounts, passwords, and User IDSs should be removed before the applications are released to the end users.
- 6.3.2: The custom codes should be reviewed before releasing to identify coding vulnerabilities, if any.
6.4
Software development companies should follow the change control process for all the changes made to the system components. These processes must include the following requirements:
- Different development and test environments from production environments
- Different duties set between development/test and production environment
- Production data must not be used for development or testing
- Test data should be removed from the system’s components before it becomes active or gets into production.
6.5
It requires the Fintech software development company and financial app developers to get trained in the secure coding methods which are aligned with the app’s coding languages. The coding techniques should be on the basis of the industry’s best practices and should be documented to ensure that the team follows them to their entirety.
6.6
Payment apps which face the public, like the web apps that can be accessed through the internet should be protected either through a Web Application Firewall (WAF) or via a stringent Web Application Vulnerability Scanning process.
Considering the importance of this PCI requirement and how it sets a minimum level of security controls, there are some security conscious organizations that opt for “belt and braces” approach within their web application security.
Why focus on PCI DSS compliance?
For new companies or startups that need to collaborate with big financial service providers, PCI DSS is non-negotiable.
The reasons concerning why they ought to consider being compliant lies in the fact that PCI improves measures in addition to increasing and showing credibility to clients and other organizations.
While it’s not important for a startup to go through a full PCI DSS compliance audit, which is possibly costly, it is beneficial getting the correct consultation to assist from a reasonable point of view and get the ball moving.
Such consultations are known as quality security assessors and they’ve been prepared and certified by the PCI Security Standards Council to help organizations conduct assessments on how they handle credit card information.
These assessors are particularly useful for new companies since they have seen genuine solutions for the most overwhelming compliance requirements.
How to Maintain PCI Compliance?
The stages of PCI DSS compliance can be accounted to be divided into two parts: The first part is to achieve a PCI DSS compliance state – which can be assured through the creation of a PCI compliance checklist – and the second part is to maintain a PCI DSS state of compliance.
The second part – staying compliant in PCI DSS is a difficult state to achieve, often because of the misassumptions that the compliance is about simply following the PCI DSS audit checklist. The formula for maintaining the compliance is to develop processes which deliver a continued PCI-compliant state.
Keeping detailed records of the security processes, and implementing the management’s oversight is a necessary approach to keep complacency from entering the system and ensuring that a PCI DSS compliance state can be verified at any point in time.
Establishing A Plan For Continuous Compliance
Continuous compliance ensures that your working environment is up to standard and fit for guarding client information. Compliance includes more than meeting all the requirements on a checklist. You need to consider how these necessities apply to your particular agenda so that you can change operations appropriately. A few stages you can take measure to guarantee continuous compliance includes:
- A Plan for Access Control
- Policy Development to Align with PCI Requirements
- Keeping and Maintaining a Detailed Records
- Oversight Management
- Regular Testing to Measure Vulnerabilities
Conclusion
With everything from end users’ security to your businesses’ future riding on the right implementation and maintenance of PCI DSS compliance, you would need to get in touch with a fintech app development company that understands the compliance’s formalities inside out. The company can be located in your native area, or it can be in any other part of the world, for example, you can choose fintech app development companies in USA. Make sure you choose the best to have quality results. In any case check the expertise and knowledge of the agency before finalizing anything.
FAQs About PCI DSS compliant Fintech Mobile App Development
Q. What are the PCI Compliance Levels?
PCI DSS is required by all organizations that store, use or transmit carholders’ data for conducting their business. But the requirements vary according to the business transactions – which divides the compliance in four levels.
Level 4: merchant processing is less than 20,000 transactions annually
Level 3: merchant processing is in the range of 20,000 to 1 million transactions annually
Level 2: merchant processing is between 1 to 6 million transactions annually
Level 1: merchant processing is more than 6 million transactions annually.
Q. What is PCI DSS?
It is a set of standards required by law directed at securing the cardholders’ data within the application and inside the organization that saves the information.
Q. What Does PCI Compliance Mean for Fintech App Business?
A Fintech app business which is PCI compliant is legally prepared to work around users’ card details for their process. Fintech companies which are not PCI compliant are not allowed to work around cardholders’ sensitive data and can face severe financial consequences like – fees, fines, and even loss of business. Consequences as these make PCI compliance software development for fintech apps an absolute must have.
Q. How to become PCI Compliant?
There are five main things that should be included in your PCI compliance checklist:
- Analysis of your compliance level
- Filling out of Self Assessment Questionnaire
- Making necessary changes/ filling shortcomings
- Completing an attestation of compliance
- Filing of paperwork
Q. Is PCI DSS Certificate Required When Using Payment Gateway?
Yes, it is required. Payment gateway integration does not relieve you of the need to acquire a PCI DSS certificate since you actually manage the payment information to a more noteworthy or lesser degree. In any case, the manner in which you add a payment gateway to your application or site will characterize the degree of compliance.
Q. What is the Relationship between PA DSS and PCI DSS?
The PA DSS is the standard for developers and the integrators of mobile payment applications who use card information for authorization and settlement of payments. In order to achieve PA DSS compliance the apps should be sold, distributed or licensed to the third parties. The compliance of PA DSS is divided into two phases –
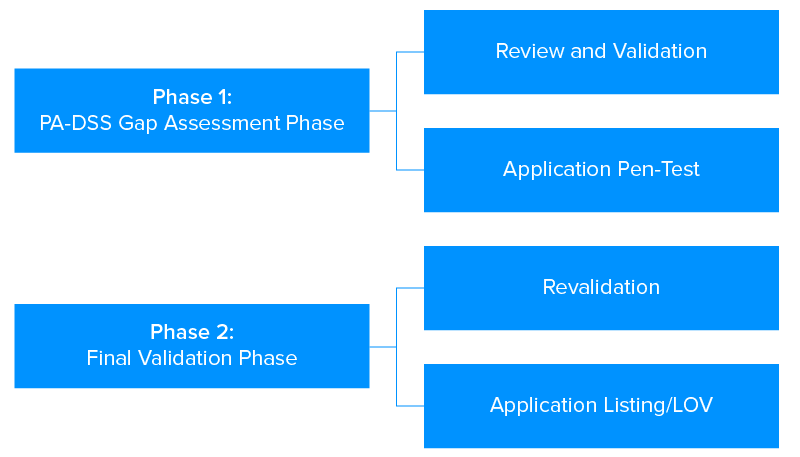
Adhering to the requirements of PA DSS is what will help you become PCI DSS compliant.

strategies your digital product..



